Scenario
A growing online retailer arrives at the office one morning to find their customer database held hostage by ransomware. They assumed their company was too small to be noticed by hackers – a dangerous misconception.
In reality, nearly two-thirds of SMBs reported experiencing a cyber breach or strong indication of one in the past year. Attacks aren’t limited to big corporations.
No organization is too small to be targeted – in fact, 60% of SMB owners rank cyber threats as a top concern, yet only 23% feel very prepared to defend against attacks. These fears are justified: nearly half of small businesses were hit by ransomware in the past year, and 61% worry a major cyber incident could put them out of business.
This landscape makes clear that every business needs a powerful cybersecurity strategy to protect its operations and data. Below, I will outline a concise framework of cybersecurity best practices and then show how the ESET PROTECT Platform can help implement this strategy effectively.
Simplify cybersecurity. Amplify protection. Claim your ESET deal now!
Key steps to a business cybersecurity strategy
A strong business cybersecurity plan doesn’t have to be overly complex. It should cover a core set of security best practices and policies that reduce your risk exposure.
Here are the essential components of a cybersecurity strategy for SMBs and enterprises:-
Risk Assessment & Asset Inventory
Start by identifying what you need to protect. Take stock of all your digital assets – from devices and servers to critical data and customer information – and assess the threats and vulnerabilities that each presents.
This risk assessment guides your priorities by revealing where your business is most vulnerable. Documenting these risks and your security policies is crucial for both internal awareness and demonstrating due diligence in the event of an incident.
-
Data Protection (Encryption & Backups)
Safeguard your sensitive data both at rest and in transit. This means using strong encryption (e.g. full-disk encryption for laptops and storage) so that data is unreadable if devices are lost or stolen. It also means maintaining reliable data backups.
Follow the 3-2-1 backup rule – keep 3 copies of data on 2 different media with 1 offsite/offline – to ensure you can recover information even after a ransomware attack or disaster.
Equally important, encrypt your backups as well, adding a layer of defense so attackers can’t access or tamper with them. Regularly test your backups to verify they can be restored in an emergency.
Deploy proven security software on all endpoints – including employee computers, servers, and mobile devices. Endpoint protection platforms (EPP) provide multilayered defenses against malware, ransomware, and hacking attempts.
They combine antivirus, firewall, intrusion prevention, and behavior monitoring to stop both known threats and new “zero-day” exploits.
-
Access Control & MFA
Protect user accounts and restrict access on a need-to-know basis. Implement strong access controls such as unique user accounts with the principle of least privilege (give each person the minimum access required for their role).
Critically, enable multi-factor authentication (MFA) on all important accounts and logins – from VPNs and email to administrative panels. MFA requires users to provide an extra proof of identity (like a one-time code on their phone) in addition to a password, which dramatically reduces the chance of unauthorized access.
-
Updates and Patching
Keep all systems and software updated with the latest security patches. New vulnerabilities in operating systems, applications, and firmware are discovered daily – over 40,000 software vulnerabilities were published in 2024, a 38% jump from the previous year.
Promptly applying updates closes these holes before cybercriminals exploit them. Enable automatic updates wherever feasible, and consider using a centralized patch management tool to monitor and deploy critical fixes across your business.
-
Employee Training and Awareness
Technology alone isn’t enough – employees play a key role in cybersecurity. Regularly train your staff on security best practices and how to spot common threats. Phishing awareness is especially important, since convincing scam emails or messages can trick even savvy users.
Teach employees how to verify sender identities, avoid clicking suspicious links or attachments, use strong passwords, and report potential incidents. Many breaches trace back to human error, so building a “human firewall” through ongoing security awareness training significantly lowers risk.
Consider running simulated phishing exercises and providing refreshers to keep security top-of-mind.-
Incident Response Readiness
Finally, be prepared for the possibility that an attack could still succeed. Develop an incident response plan that defines clear steps for containing and recovering from security incidents (like a malware outbreak or data breach).
This plan should assign roles (e.g. who coordinates response, who communicates with customers/regulators, etc.), outline key actions (such as isolating affected systems, restoring backups, contacting law enforcement or cyber insurers if needed), and include an after-action review to improve defenses.
Being ready to react swiftly can mean the difference between a minor security event and a business-ending disaster.Next, I’ll look at how to put this strategy into action using ESET’s solutions.
ESET PROTECT Platform with your cybersecurity strategy
Implementing a strong strategy is much easier with the right tools. The ESET PROTECT Platform is a unified cybersecurity solution that helps businesses address all the above areas with a single, integrated suite.
ESET has a long-standing reputation in security software, and its business platform offers centralized management and a full stack of protective technologies.
Here’s how ESET PROTECT can serve as the engine of your cybersecurity strategy:-
Centralized Management & Visibility
At the heart of ESET PROTECT is a centralized management console that gives you complete oversight of your network security. From one cloud-based dashboard, IT administrators can deploy security to endpoints, enforce policies, monitor threats, and respond to incidents across all your devices.
This “single pane of glass” approach provides superior visibility and control. In fact, ESET’s console maintains an up-to-date inventory of your hardware and software assets, so you always know what devices and applications are in your environment.
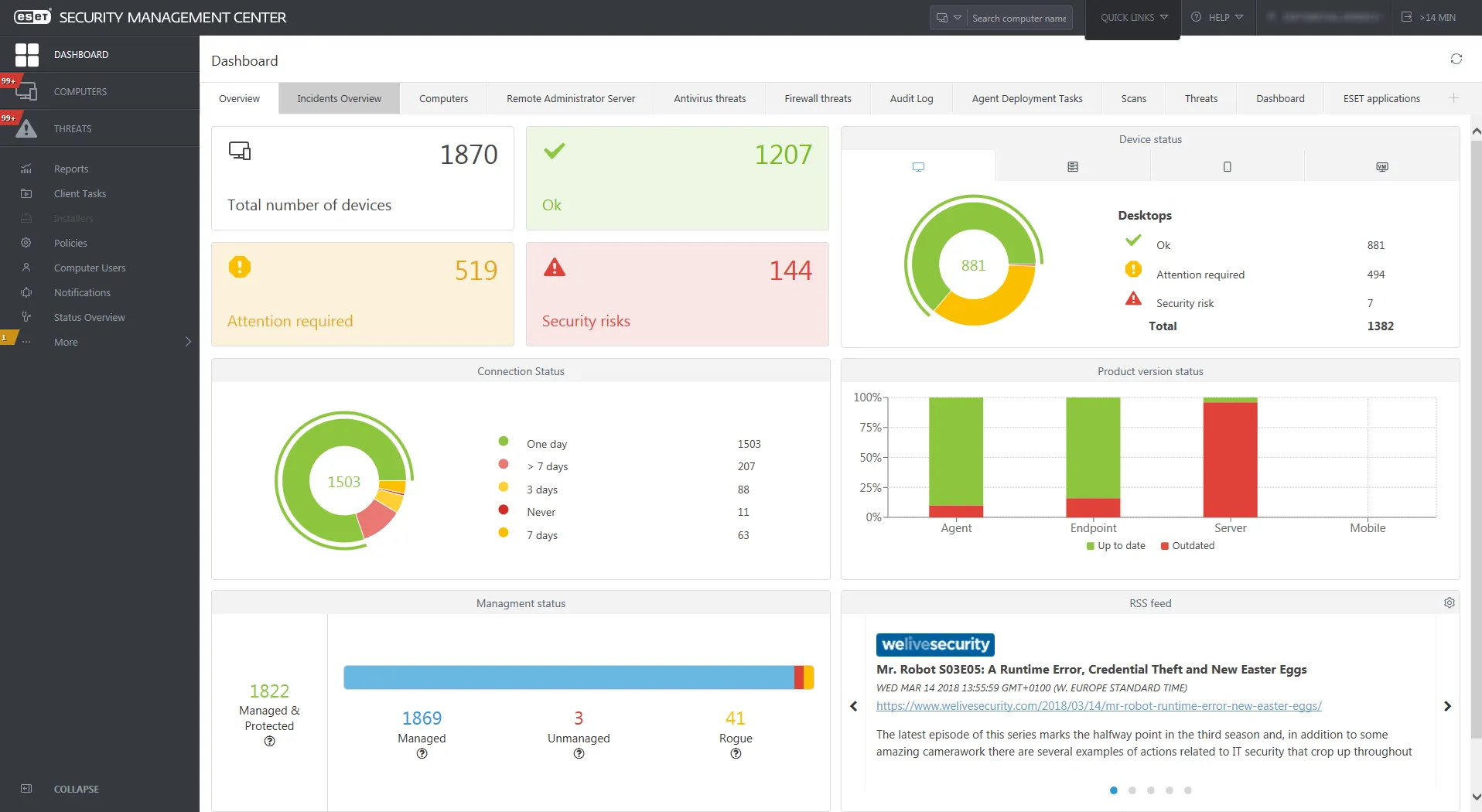
In short, ESET makes it straightforward to implement your security policies consistently across the organization, which is essential for risk management and compliance.
-
Multi-layered Endpoint Protection
ESET’s core strength is its multi-layered endpoint security, which forms the core of protecting your computers, servers, and mobile devices. ESET Endpoint Protection uses a combination of signature-based malware detection, heuristics, behavior analysis, cloud sandboxing, and machine learning to catch both known and emerging threats.
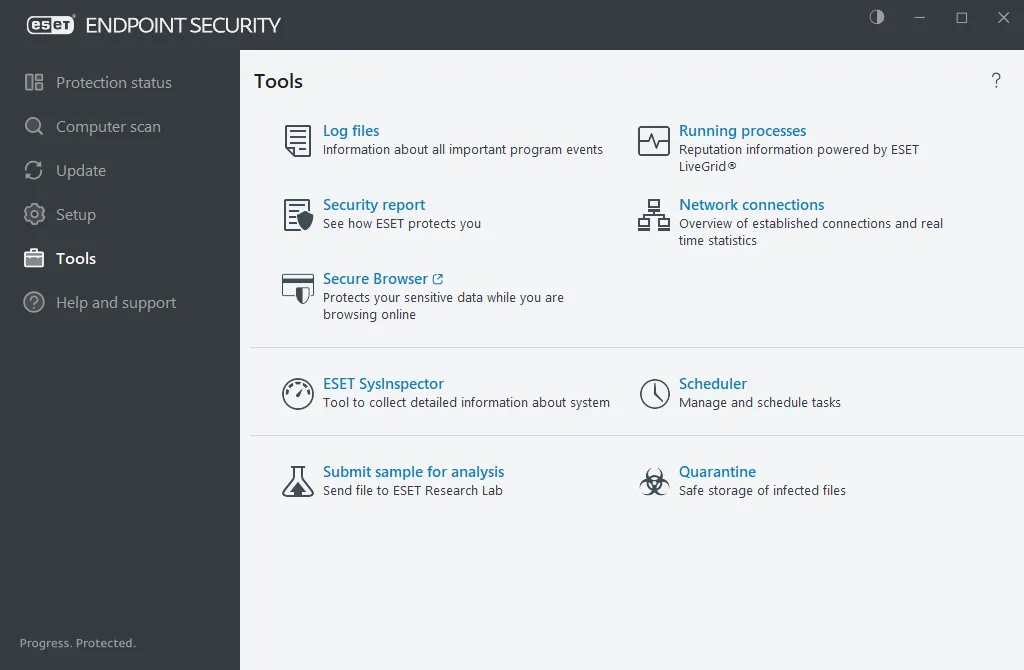
This multilayered approach means threats are stopped at various stages – from blocking malicious URLs and email attachments (phishing protection), detecting exploit attempts, to neutralizing ransomware and rootkits before they can execute.
Thanks to its lightweight design, ESET’s antivirus runs with minimal system impact, so it won’t slow down your business devices.
-
Data Encryption and Device Control
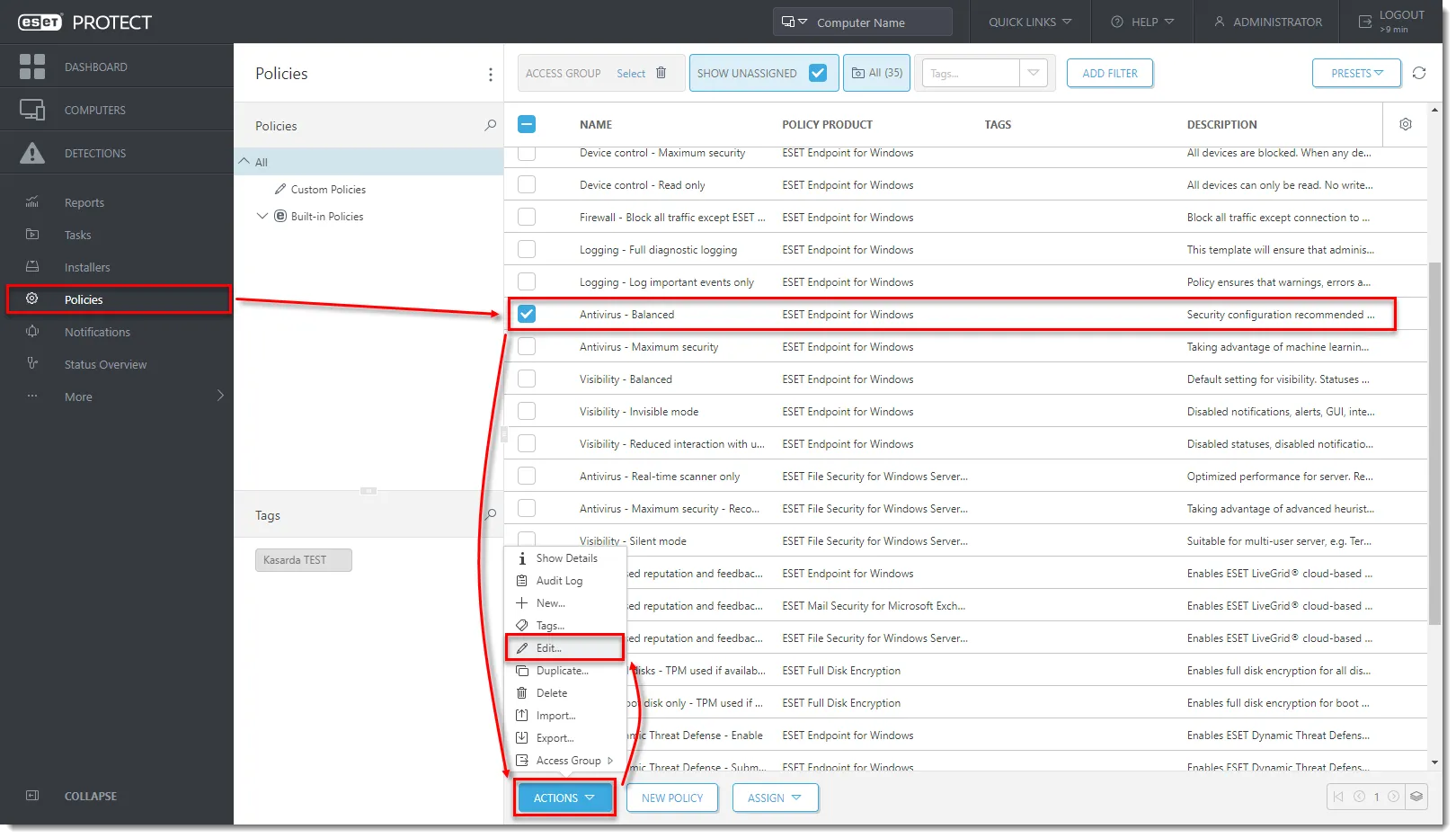
To protect sensitive data, ESET offers built-in encryption tools that integrate with the PROTECT management console. ESET Full Disk Encryption allows you to encrypt entire hard drives, partitions, or portable media at the click of a policy, helping ensure that confidential data can’t be read if a laptop is lost or stolen.
This is vital for regulatory compliance and data privacy requirements. The encryption is managed centrally via the console – you can deploy encryption to endpoints and monitor compliance from the same dashboard.
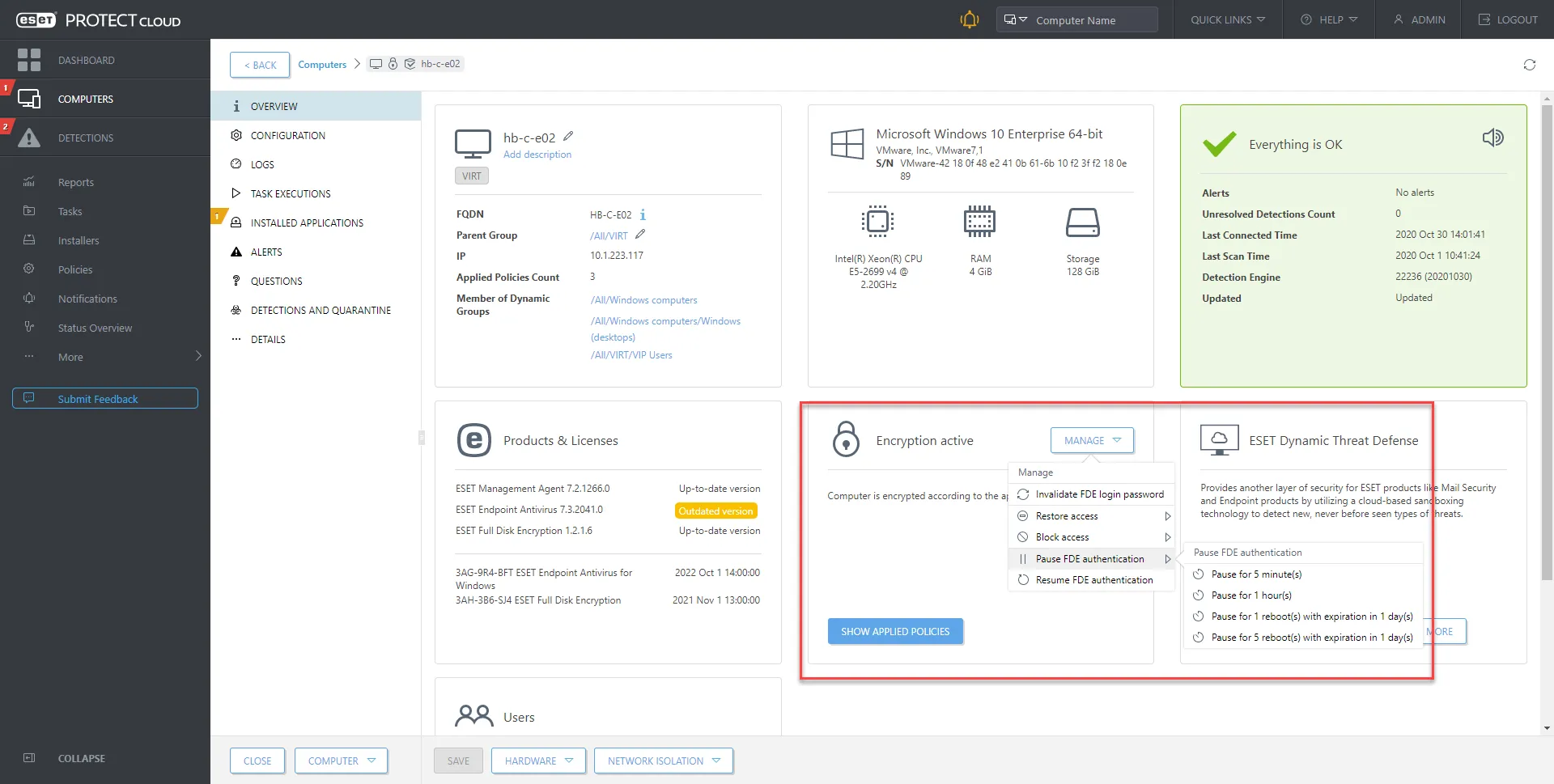
In addition, the ESET platform includes device control features, letting you set rules for USB drives or other removable media (for example, blocking unapproved USB devices from copying data).
While ESET doesn’t itself provide a backup solution, it complements data backup strategies – for instance, ESET’s Ransomware Shield and remediation can safeguard backups by preventing malware from encrypting or deleting those files.
-
Identity & Access Security (MFA & Account Protection)
ESET PROTECT also helps you implement strict access controls. It supports integration with multi-factor authentication via ESET Secure Authentication (a mobile-app-based MFA) to harden logins to the console and other business systems.
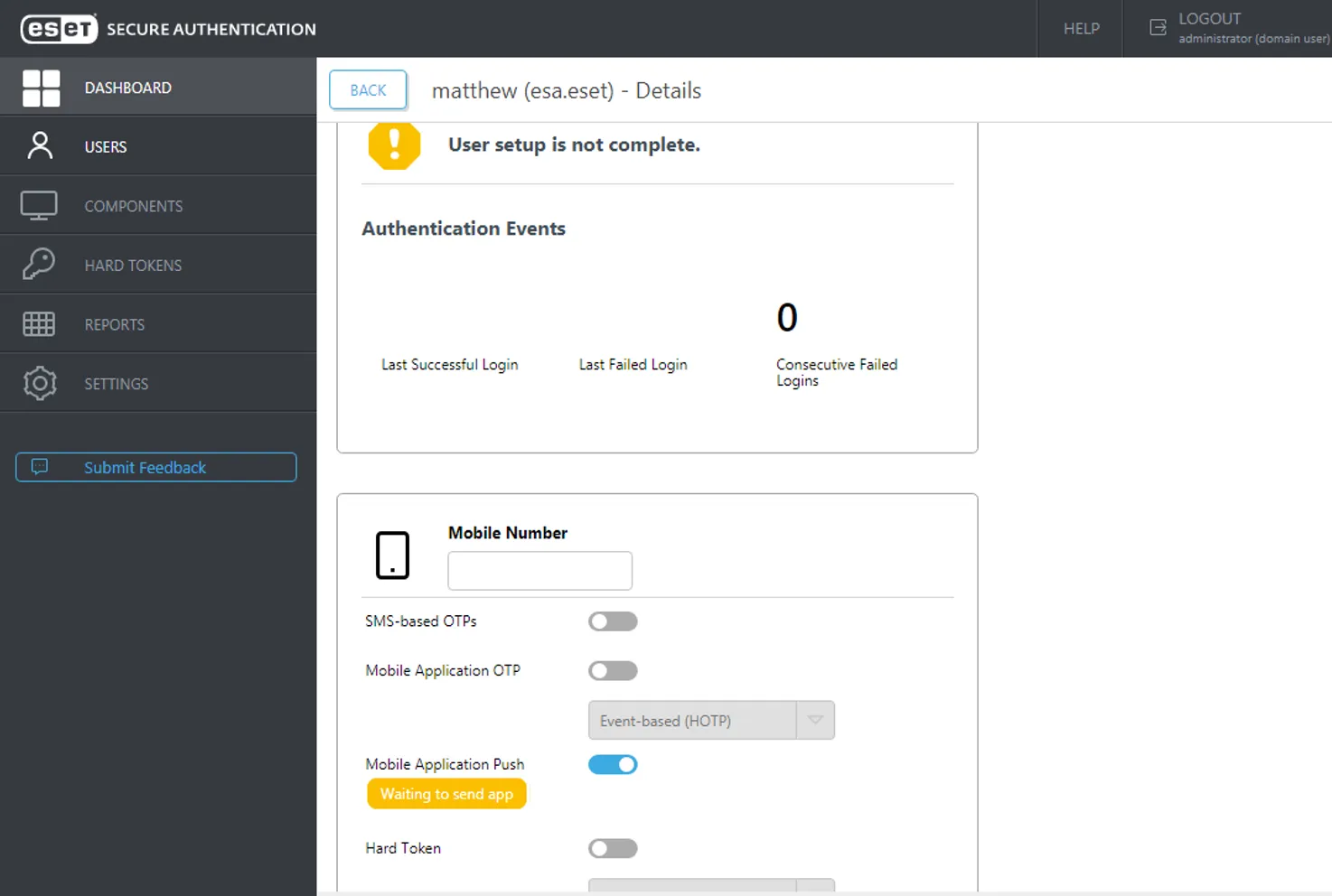
The platform’s single-tap MFA solution is easy for employees to use and dramatically reduces the risk of account compromise by adding a one-time code verification on top of passwords.
Additionally, ESET’s endpoint security includes features to prevent brute-force attacks and credential theft – for example, network attack protection and botnet protection that can block attackers trying to hijack accounts.
-
Email & Cloud Application Protection
Phishing and email-borne threats remain among the top risks to businesses, so ESET provides specialized email and cloud security solutions to address this vector.
As part of the PROTECT platform, ESET Mail Security can be deployed on mail servers (e.g. Microsoft Exchange) to filter out spam, malware attachments, and phishing emails before they reach inboxes.
For companies relying on cloud services like Microsoft 365 or Google Workspace, the ESET Cloud Office Security (now under Cloud App Protection) module safeguards cloud email and storage as well.
It scans emails, OneDrive/SharePoint files, and Teams/Google Drive for threats and prevents infected files or links from causing harm.
-
Vulnerability & Patch Management
Keeping systems updated is a breeze with ESET’s vulnerability and patch management features. ESET PROTECT includes a module that automatically scans your endpoints for missing patches in Windows and hundreds of common applications.
From the central console, you get reports on which machines or software are vulnerable, and you can push out patches enterprise-wide with a few clicks.
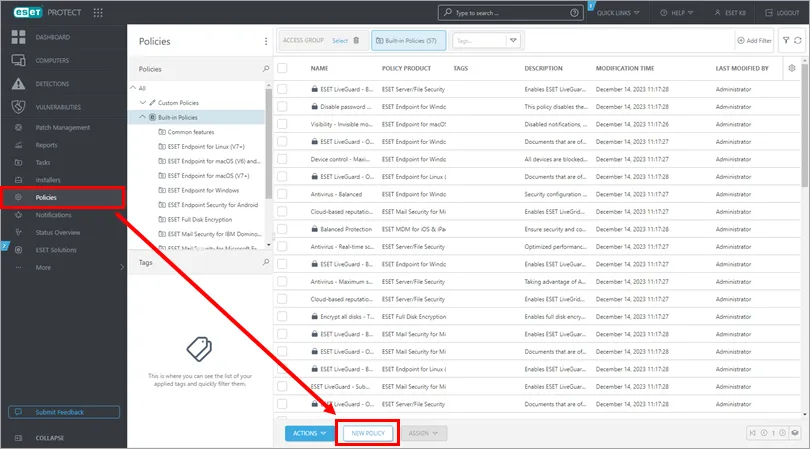
The solution lets you prioritize updates by severity, schedule maintenance windows, and even set automatic patch deployment for critical fixes. By actively tracking known vulnerabilities and keeping a real-time inventory of software versions, ESET helps ensure no machine is left dangerously out-of-date.
Patching is one of the most effective ways to prevent attacks (since attackers often exploit unpatched flaws), and ESET’s tool makes it practical even for small IT teams to stay on top of this task.
You’ll enjoy complete visibility into your patch status across the organization – a key benefit when auditors or clients ask for proof of vulnerability management.
-
Advanced Threat Detection & Response (EDR/MDR)
Cyber threats are getting more sophisticated, so beyond prevention, businesses should have capabilities to detect and respond to incidents quickly.
ESET addresses this through its Extended Detection and Response (XDR) and Managed Detection and Response (MDR) services.
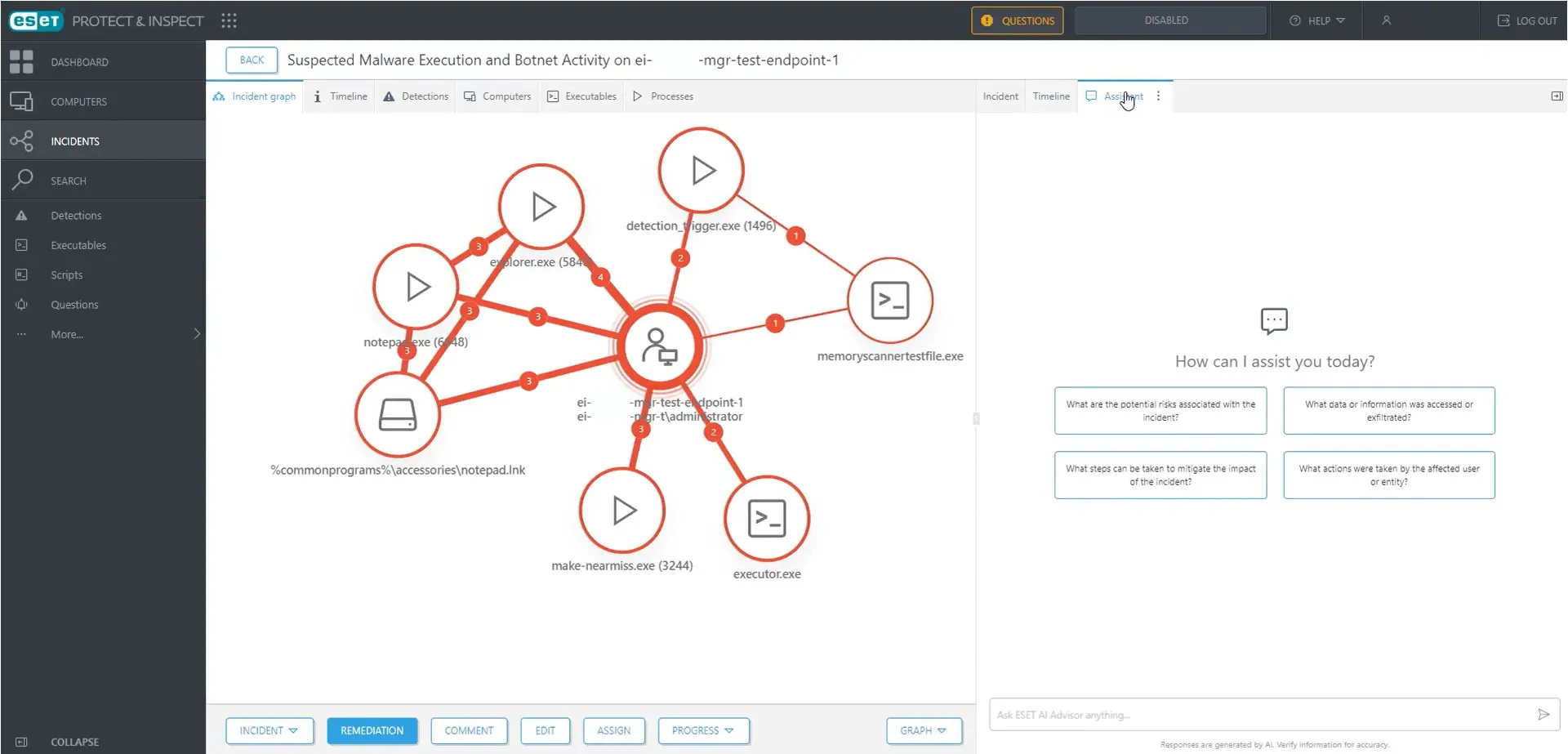
ESET’s XDR solution, called ESET Inspect, is integrated into the PROTECT platform to monitor endpoint and network behaviors for signs of an intrusion. It uses analytics and threat intelligence to flag anomalies or suspicious patterns that might indicate a stealthy attack or breach.
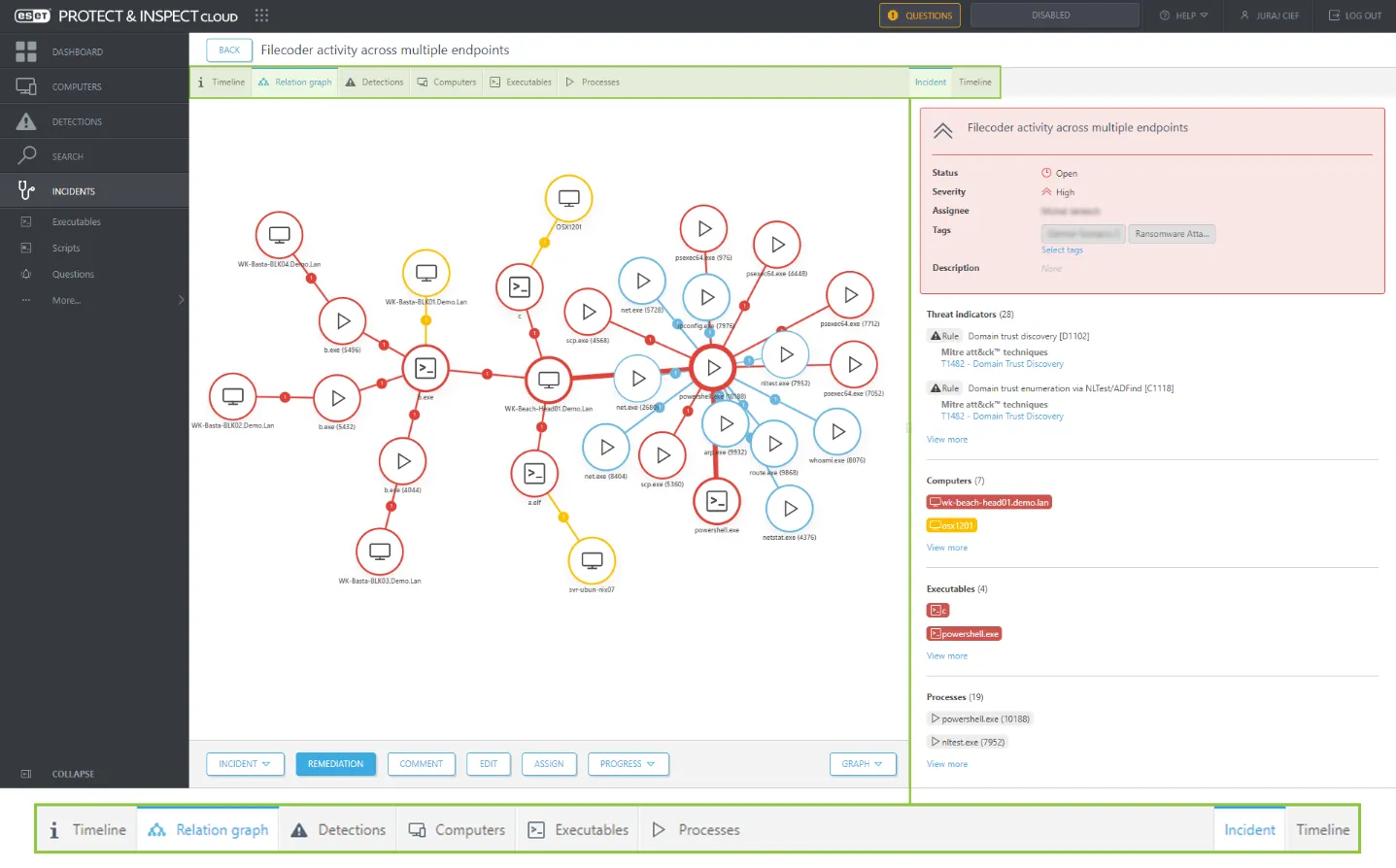
For organizations without a dedicated security operations center, the ESET MDR service provides 24/7 threat monitoring and incident response by ESET’s own experts.
In practice, this could limit damage from a breach, as ESET will help you stop attackers early and guide you through recovery steps.
-
Ease of Deployment & Support
A cybersecurity solution only adds value if it can be deployed and managed without headache. ESET excels here by offering flexible deployment options and top-notch support.
You can run ESET PROTECT Platform as a cloud-based service (ideal for ease and low overhead) or as an on-premises server if required, with support for all major operating systems – Windows, macOS, Linux, Android, and iOS.
Setting up ESET is straightforward, and its small footprint ensures even older machines can run the security software smoothly. When it comes to support, ESET has a solid reputation: business users often highlight the responsive technical support and local partner network ESET provides.
When you pick a solution that is simple to manage, it becomes easier to keep your security measures up to date and set up correctly. This makes your cybersecurity strategy stronger. ESET’s emphasis on usability and support helps turn your best practices into daily habits.
Key Takeaways & Next Steps
- Cover the fundamentals: Every business cybersecurity strategy should address the basics – know your assets and risks, protect data with encryption and backups, secure all endpoints, control access with MFA, keep systems patched, educate your users, and prepare for incidents.
- Leverage Multi-Layered Solutions: Implementing multiple defensive layers is crucial. ESET’s PROTECT platform exemplifies this by combining prevention (anti-malware, firewall, phishing filters), detection (XDR analytics), and response (MDR service) in one suite.
- Centralize and Simplify: Using a unified security platform like ESET PROTECT allows you to manage cybersecurity in a consistent, efficient way. Central visibility and control translate to faster responses and easier enforcement of policies across the organization – a big advantage for SMBs with limited IT resources.
- Stay Proactive: Cybersecurity is not a one-time project but an ongoing process. Regularly review and update your strategy as new threats emerge or your business IT changes. Take advantage of tools (such as ESET’s cloud console and reports) to continuously monitor your security posture. Being proactive – from user training to threat hunting – will keep you ahead of attackers.
Don’t wait for a breach. Prevent it. Try ESET PROTECT now!
Final Verdict
Building a strong business cybersecurity strategy is one of the best investments you can make in your company’s future. The good news is that you don’t have to tackle this alone or reinvent the wheel. Trusted cybersecurity solutions like the ESET PROTECT Platform are designed to help businesses of all sizes implement effective security with relative ease.
Don’t wait for a cyber incident to test your defenses. Take the initiative to evaluate how ESET can fortify your company’s cybersecurity strategy.Consider launching a free trial or contacting ESET to see firsthand how their multi-layered security solutions can safeguard your business. By investing in the right cybersecurity measures now, you set your organization up for safer growth in the digital world.







